Spearphishing

No, this article is not really about fishing, but about the most common form of Internet exploits that we are seeing today. In fact, over 50% of all Internet attacks take a form called Spear Phishing. Phishing is an attempt to acquire information from a target by impersonating a person or organization in an electronic message and motivating the target to either open a malicious attachment or connect to a linked website containing malicious files. Spear Phishing refers to Phishing targeting specific individuals or companies.

Targets that open these malicious attachments or connect to these linked websites can have spyware installed on their workstations to compromise their usernames, passwords, address books, banking accounts, and other information sought by the perpetrators of these attacks. Compromised accounts are often used to distribute spam to new targets, often identified in the target's address books, people who will recognize the sender and open messages or attachments thinking they are from a trusted associate.
Spear phishing has become so predominant because of the ease with which it can be employed against anyone. All someone needs to have to attack you is your email address. They can get it from websites where you may have posted it or from your friends and business associates if their workstations are compromised.
Many of the spear phishing messages may look authentic and may include genuine graphics and content copied from the actual organizations being impersonated. these include banks, electronic commerce sites, PayPal, phone companies, Internet service providers, Federal Express, DHL, the US Postal Service, or similar businesses. The common thread to watch for is a sense of urgency in their message urging immediate or impulsive action involving opening an attachment or connecting to a website.
Others may include links to web sites that impersonate Canadian pharmacy sites or social media. Fake Canadian pharmacy sites are popular with the Russian mafia and are used primarily to harvest credit card numbers from unwitting customers. None of these sites actually sell anything; they exist only for large scale mining of credit card numbers.
Secondary markets have developed where stolen user accounts and credit cards are bundled into groups of thousands of entries and resold to other attackers. Malicious software is also developed and sold making it easy for anyone interested in engaging in this activity to acquire the tools and information they need to conduct their intended purposes.
Most Spear Phishing attacks are so naive that it is easy to dismiss them as serious threats; however their popularity with criminal organizations and hostile foreign agencies is the result of their success. These attacks are easily automated and conducted on a large global scale. The attackers only need a small percentage of these attacks to succeed in order to yield the desired results.
The best defense against Spear Phishing is prevention. Protect your email accounts from exposure. Use different accounts for different purposes. Delete suspicious messages without opening attachments or clicking links. Legitimate businesses such as Banks do not operate using email messages. Feel free to contact us if you have any questions or assistance.
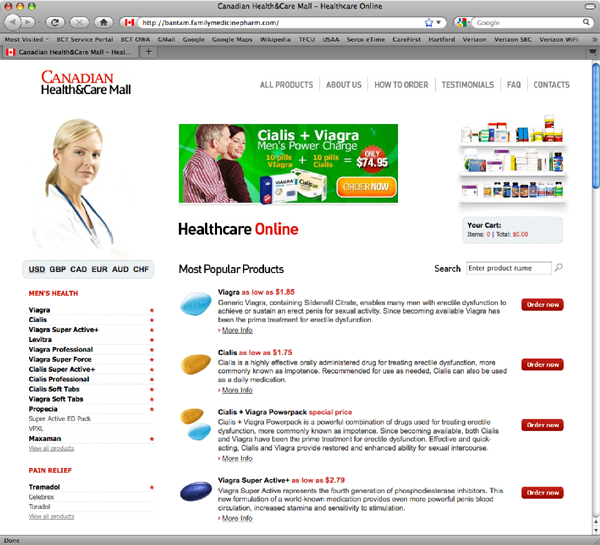
This is an example of a typical fake Canadian web site, actually operated by the Russian Mafia to steal credit card numbers.
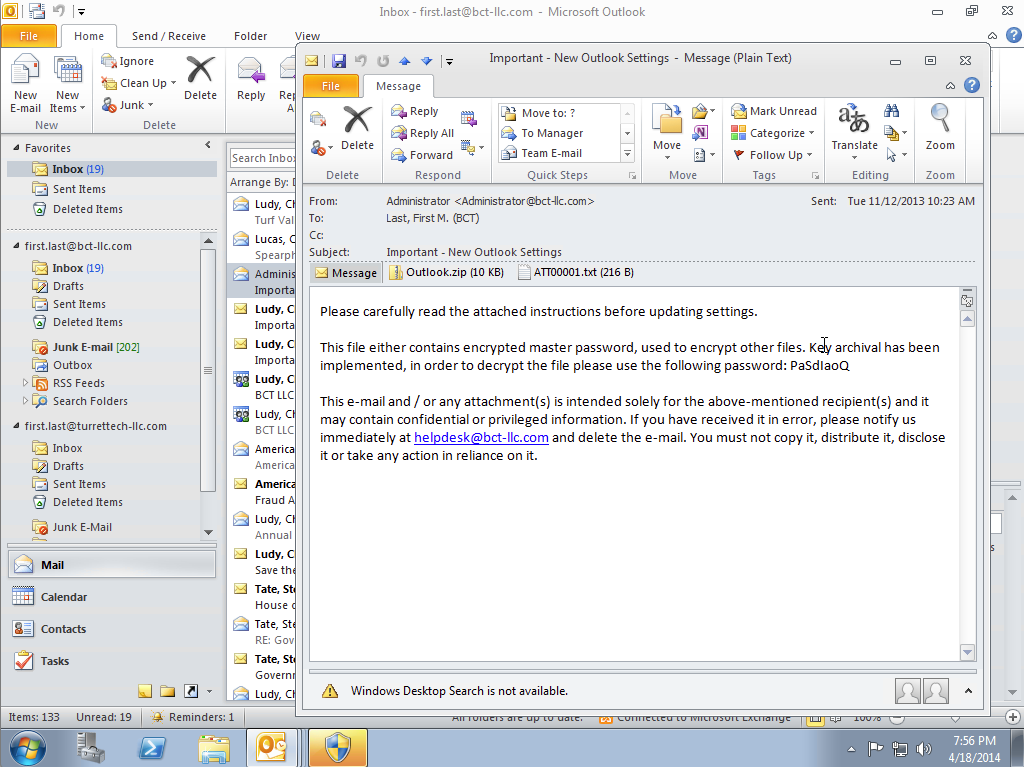
This is an example of a typical fake administrator message, actually operated by the Russian Mafia to compromise your system. Remember we never send security messages by emails, and we never use generic administrator accounts.
Defense Security Service (DSS)
DSS's Center for Development of Security Excellence (CDSE) has released a new Counterintelligence (CI) Security short, "Suspicious Emails." This short provides learners with an opportunity to practice identifying what constitutes a suspicious email while increasing awareness about the importance of reporting suspicious contacts. To access the new CI short, go to:
Better Business Bureau
These videos produced by the Better Business Bureau provide more information about today's Phishing and Identity Theft threats.
 Better Business Bureau Video: Avoiding Internet Phishing
Better Business Bureau Video: Avoiding Internet Phishing Better Business Bureau Video: Phishing Scam Protection
Better Business Bureau Video: Phishing Scam Protection Better Business Bureau Video: Avoiding Phishing Scams
Better Business Bureau Video: Avoiding Phishing Scams Better Business Bureau Video: Technology and Identity Fraud
Better Business Bureau Video: Technology and Identity Fraud